The two terms often used in tandem for access control in almost every system but they are inherently different. In this article i will try to explain difference between these two terms.
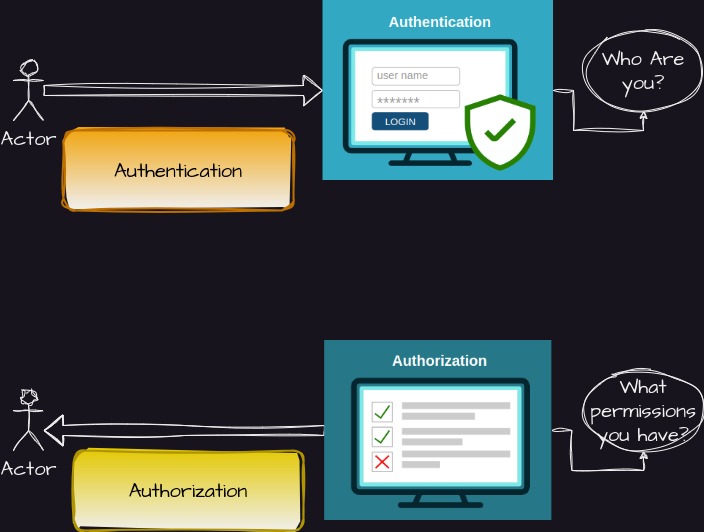
In simplest terms, Authentication is the process of verifying the identity of a user or system requesting access to an API, while Authorization determines what actions and resources a user or system is allowed to access within the API based on their authenticated identity. Let us see each of it one by one.
Authentication
Authentication is the process of verifying that a user is who they claim to be. To prove identity in a system, one need to provide them with valid credentials like the username and password. Authentication typically involves the exchange of credentials (e.g., username and password, API key, or token) between the client (requesting entity) and the server (API provider) to verify the identity of the client. This process ensures that only authenticated and authorized clients can access the API’s protected resources. Common authentication mechanisms include OAuth, JWT (JSON Web Tokens), API keys, and basic authentication.
-
OAuth: A widely adopted protocol that allows users to grant limited access to their resources on one website (known as the provider) to another website (known as the consumer) without sharing their credentials. OAuth uses tokens to authenticate requests and maintain secure communication.
-
JWT (JSON Web Tokens): A self-contained, digitally signed token that carries claims about the user or system. JWTs are commonly used for authentication, allowing clients to present their token with each request to gain access to protected resources. They eliminate the need for server-side session storage, enhancing scalability.
-
API Keys: A simple and commonly used method where clients provide an API key, usually in the form of a unique string, as part of their requests. The server validates the key to authenticate the client. API keys are easy to implement and provide a basic level of security.
Authorization
While authentication verifies the identity of a client, authorization determines what actions and resources that client is allowed to access within the API. Authorization ensures that only authorized clients can perform specific operations based on their authenticated identity. Key concepts related to API authorization include:
-
Roles and Permissions: Establishing a role-based access control system where users or systems are assigned specific roles (e.g., admin, user, guest) with corresponding permissions. This approach allows fine-grained control over the API resources and operations available to different client types.
-
Scopes: Implementing scopes or privileges associated with specific API endpoints. Clients are granted access to certain endpoints based on the defined scopes they possess. This approach allows for more granular control over the level of access granted to clients.
Best Practices for API Authentication and Authorization
To ensure robust security for APIs, it is crucial to follow industry best practices:
-
Strong Encryption: Use secure communication protocols such as HTTPS/TLS to encrypt data transmitted between clients and servers, protecting it from eavesdropping and tampering.
-
Token Management: Employ proper token management techniques, including token expiration, token revocation, and secure token storage. Regularly rotate and refresh tokens to mitigate the risk of unauthorized access.
-
Multi-Factor Authentication (MFA): Consider implementing MFA mechanisms, such as SMS-based verification codes or biometric authentication, to add an extra layer of security.
-
Regular Security Audits: Conduct periodic security audits and vulnerability assessments to identify and address any potential weaknesses in your authentication and authorization processes.
Closing Remarks
API authentication and Authorization are fundamental pillars of securing APIs. Properly implementing these processes ensures that only authenticated and authorized clients can access protected resources, safeguarding sensitive data and preventing unauthorized actions. By leveraging robust authentication mechanisms like OAuth, JWT, and API keys, combined with effective authorization strategies such as role-based access control and scopes, developers can establish a secure API ecosystem. Following best practices and staying updated with evolving security standards will help maintain the integrity and confidentiality of APIs in an ever-changing digital landscape.
-
Previous
Building Secure Apis Safeguarding Data and Trust -
Next
Essential Questions to Ace Your Next DevOps Job Interview